Introduction
This article explains setting up the PGP connector and encrypting and decrypting the data using the PGP keys.
Pre-requisite
It is assumed that readers of this article know how to create integrations on webMethods.io integration.
What is PGP?
• Pretty Good Privacy (PGP) is a security program used to decrypt and encrypt messages and authenticate them through digital signatures.
For more details, please refer Pretty Good Privacy - Wikipedia
How PGP works?
• PGP works through a combination of cryptography, data compression, and hashing techniques.
• It is similar to other popular encryption methods such as Kerbos, which authenticates network users, secure sockets layer (SSL), which secures websites, and the Secure File Transfer Protocol (SFTP), which protects data in motion.
Encryption and Decryption
• PGP uses the public key system in which every user has a unique encryption key known publicly and a private key that only they know.
• A message is encrypted when a user sends it to someone using their public key, then decrypted when the recipient opens it with their private key.
• It combines private-key and public-key cryptography and the use of symmetric and asymmetric key technology to encrypt data as it travels across networks.
Use case:
• In our use case we will encrypt the data in webmethods.io flow service using PGP keys and will store the encrypted data in some cloud location. In our case, we are going to use the Azure Blob storage as our storage.
• Encryption will be done using the public key
• Once the encrypted data is stored in Azure storage location. We will pull the data from Azure storage and will decrypt it using the PGP private key.
Connector Used
• PGP connector used for encryption and decryption of data.
• Azure storage connector used for storing and retrieving the data.
Create a PGP connector account in webMethods.io Integration.
• In our case we have created the PGP keys and certificates using
https://pgptool.org/
• From the above tool we have generated the public key, private key and passphrase.
• When we were configuring the PGP account we supplied the same details.
Flow Service to Encrypt the message.
• In this flow service we have encrypted the data and uploaded it to a third-party storage location. In this case, we have Azure data as a storage location.
• You can use any storage location for uploading the data.
• A private key is not required to encrypt the message. Encryption is done using the public key.
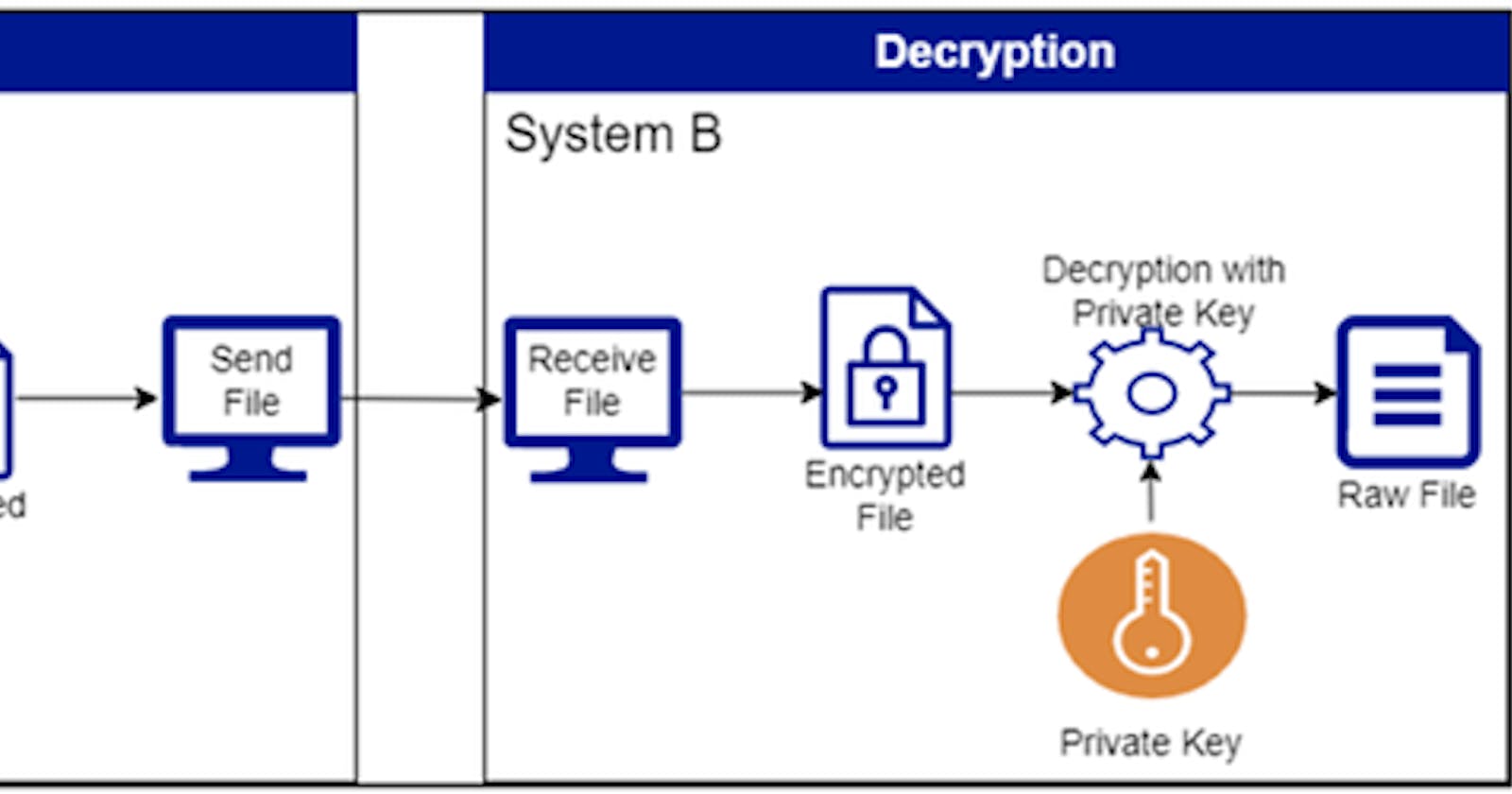
Flow Service to Decrypt the message *
• In this flow service we are pulling the encrypted data from the Azure storage location.
• Decrypting the message using the private key corresponding to the public key with which we have encrypted the message.
• Private key is mandatory to decrypt the message.
Note:
Attached are the flow services used for the encryption and decryption of the messages.